One of the fundamentals of using electronic media these days boils down to the need for protection against ubiquitous online perils. Thankfully, users don’t have to reinvent the wheel in this context, because such a protection already exists and is readily available to everyone. Its name is VPN.
This post is aimed at familiarizing you with virtual private networks and busting some of the top VPN misconceptions.

source:blog.bolehvpn.net
Page Contents
Myth 1: VPN will slow down Internet connection
This may hold true to a certain extent, but the evolution of this tech is underway, and the speed is growing. In fact, a small decrease in the connection speed isn’t likely to become a reason to sacrifice your online security altogether.

source:blog.bolehvpn.net
The speed depends on quite a few variables. The most common one is the whereabouts of the server you select. The larger the distance from your current location to the server, the slower the connection. This is why it’s preferable to choose a VPN service with numerous servers around the globe. There are actually plenty of ways to increase your VPN speed, please read here about them.
Myth 2: Why purchase a VPN if there are plenty of free ones?
Commercial VPNs will meet your expectations and ensure a high level of security. As a result, most attempts of cybercriminals to intercept and interpret your data will end up futile.
One of the ways free VPN providers monetize their services is through tracking your online activities and retaining logs of everything you do on the Internet. In other words, even if crooks cannot spy on you, the provider can. This fingerprintable information will probably be sold to a third party afterward.
source:liquidvpn.com
One of the criteria for choosing a free VPN is a strict no-logs policy, which means the vendor doesn’t harvest and store your sensitive data. Also, make sure the service doesn’t leak any customer information.
Myth 3: All VPNs don’t really differ from one another
When it comes to the basic features, that’s true – all virtual private networks accommodate data encryption functionality and provide a secure connection. Nevertheless, the technical characteristics of different VPNs vary.
To begin with, there are many techniques to encrypt traffic. Furthermore, the services can use different protocols to safeguard the connection between the device and VPN servers. These protocols include OpenVPN, PPTP, and L2TP.
OpenVPN is a protocol based on open source technology and ensures a high degree of anonymity and data security.
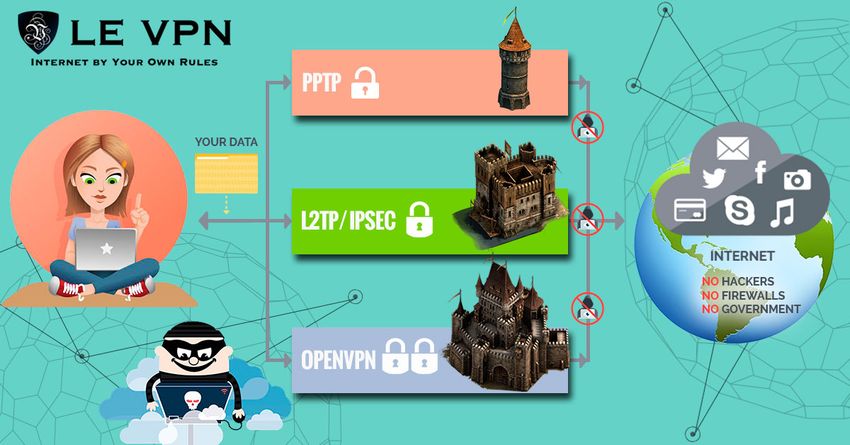
source:le-vpn.com
PPTP is less secure as it doesn’t always employ crypto. Therefore, it’s not the optimal way of transferring sensitive information. Meanwhile, it has a number of benefits. It works great for accessing geo-restricted content, doesn’t reduce download speed and allows you to view streaming videos without lags.
L2TP boasts a high level of connection security, which makes it a dependable protocol for transferring valuable data.
Myth 4: VPN protects me from all online threats imaginable
Whereas VPN provides a solid layer of defense against numerous menaces on the Internet, it doesn’t take care of all of them. For instance, it won’t keep you safe if you click ads leading to malicious sites or download suspicious email attachments that may infect your device with viruses or steal your identity via phishing.
In other words, even if you use VPN you are still better off additionally leveraging an effective antivirus tool that will fend off harmful code. Also, be sure to maintain backups of the most important data and keep your operating system up to date.
Myth 5: VPNs make my web surfing absolutely anonymous
The vast majority of VPN providers claim they don’t retain logs. However, that’s a misconception. If they didn’t store any logs at all, they wouldn’t be able to provide tech support to their customers.
No tool or company can deliver ultimate online anonymity, and it’s a major delusion to think otherwise. Even if a VPN service of choice is diligently protecting your data, there are always individuals who want to get hold of it.

source:le-vpn.com
Myth 6: Tor and VPN are equally secure
Tor (The Onion Router) and VPN actually share some functions, but the types of connection are different. In the case of a VPN, your own device is the starting point where data encryption and secure connection occurs, and it ends on the endpoint device.
With Tor, though, your ISP is an obligatory link in the connection chain. It’s not until you connect to its network that your data can stream through a secure channel. When the information reaches its destination, it has to leave the Tor network. In other words, your traffic is potentially exposed to interception before and after you connect to Tor. As opposed to that, VPNs ensure uninterrupted security throughout the data transferring process.





